Features
- Lectures – 38 Nos
- Duration - 19 Weeks
- Case Studies and Assessment - 15+
- Delivery Mode - Online/Offline
- Batches - Weekdays/Weekend
- Capstone Projects - 10+ projects (Choose anyone)
Cybersecurity is one of the most searched terms in the current generation. Cyber security may be defined as the practice of defending the system, networks, programs, and vital information of a person or any organization from continuously increasing malicious threats and cyber-attacks. Cyber security experts use various methods and technologies to put a stopper to such kinds of attacks and safeguard information.
With each passing day, Cyber criminals are becoming more and more equipped and sophisticated. So, the rate of intrusion is increasing rapidly and all the organizations are showing concern towards the safeguarding of their data and this is the reason the Cyber security domain is experiencing huge growth and demand. The Bureau of Labor Statistics has predicted a whooping growth of 28% in the domain of Information security between the year 2016-2026 and it’ll be opening a larger scope for information security analysts or cyber security specialists.
Program Overview
- This cybersecurity certification program is the most comprehensive curriculum with training material designed by NASSCOM, along with its 35 SIG(Special Interest Group) members such as Goldman Sachs, IBM, Ins Analytics, Infosys BPO, Insights of Data, JP Morgan, Karvy Analytics, Knod Global, KPMG, Wipro, WNS, Wells Fargo, Amazon, Capgemini, Concentrix, CITI, Cyient Insights, Accenture, EXL, First America, Fractal Analytics, GENPACT, Google, ADP Deloitte, HCL, HDFC, IBM, ISC2, NIIT University, PwC, Symantec, TCS to name a few, that will prepare you for future externalities in the data analytics industry and fulfill the gap of academics and industry requirements. This official NASSCOM-CERTIFIED Cyber Security Program covers all the demanded Cyber Security tools, including Python, Java, AWS, OWASP, Burp Suite, Snort, Wireshark, MetaSploit, and many more.
Cyber Security Program Certification Structure
This Nasscom Certified Cyber Security program will cover in-depth knowledge and will give proficiency over more than 25 tools and skills to undertake any problem efficiently on the organizational level. This course will help the learner to lead a successful career in the field of cyber security.
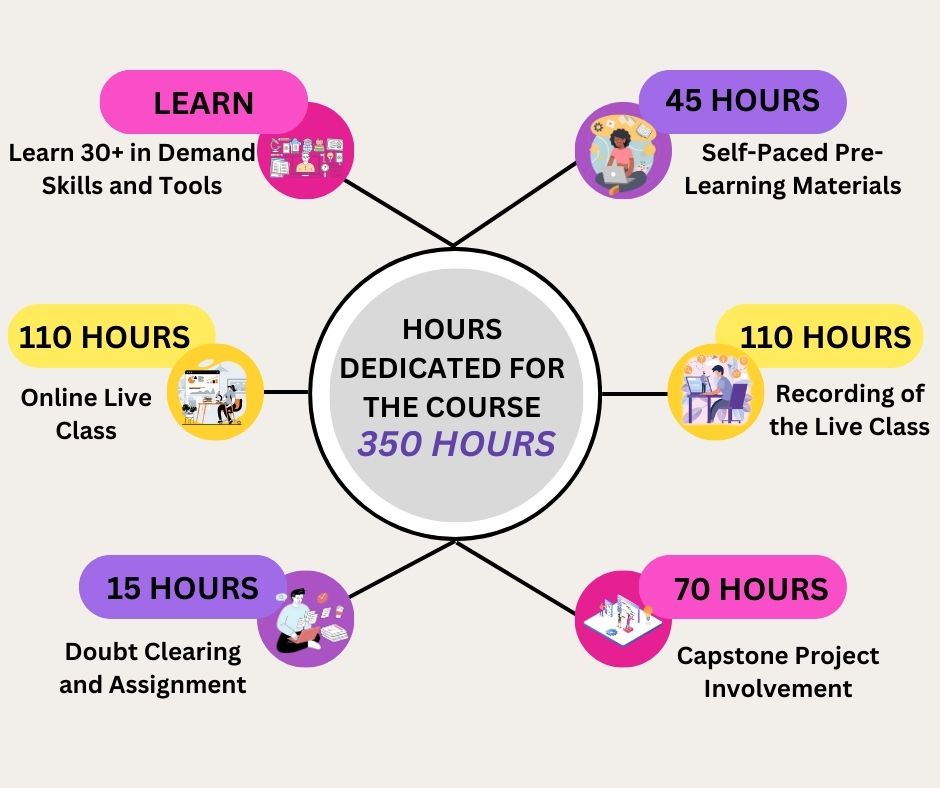
- This sophisticatedly designed 350-hour cyber security curriculum has been bifurcated into five different segments to help the learner grasp everything smoothly.
- 50-Hour Pre-Learning: Before you come in, get ready for the Program. You will get a series of online recorded tutorials to understand the structure of cybersecurity
- 114 Hours Program: Here, you will get Hands-on Experience with various Cyber Security tools and techniques which includes IAM, LDAP, CAPTCHAS, DDos Attack, Botnet Attack, SQL Injection, Hashing, Encryption, Firewall, Metasploit, Packet Inspection, ICMP Attack, Vulnerability Management, Indian Cyberspace and Laws, Cyber Security Framework, CIA and many more.
- 186 hours Post Program: Learning does not stop here. After completing the Program, you will work on Projects and assignments. Doubt clearing is also provided. You will be working on any one capstone project from the list of a few projects of your choice. You also will get the recording of the class.
Price :
- Elective 1: Advanced Data Science and Neural Network, INR 24999+GST, $407
- Elective 2: Advanced Business Intelligence, INR 11,999+GST, $220
Eligibility:
This cyber security program has been curated carefully to ensure the smooth learning of the enrolled candidates. It will help the learners to match the various hierarchical requirements of various organizations working in the cyber security domain. It’ll help the learner to know the current world scenario, demand and need of cyber security and, the use of various tools to solve problems.
Work Experience
This program will help the senior and mid-senior level managers of the cyber security domain to make efficient decisions for the organization. This course can also be opted by any young or mid-level IT professionals looking for a transition into the domain of cyber security. A fresh graduate of any stream wants to join the cyber security domain and start a career. It can be a choice for any senior professional involved actively in the cyber security practices of any organization.
Sample Certificate

Nasscom Certificate –

-
Fundamentals of information security
Introduction and importance to information security, elements of information security, support and operation, security awareness, responsibilities rights and duty. Principle of Information security (Confidentiality, Integrity, Availability), data security and types, strategy, Information security controls, types of controls, Kevin Mitnick’s Website's XSS Vulnerability.
Network Security, Firewall, Types of Firewalls, Types of Network Security Attacks, Network Vulnerabilities, Tools Used to Ensure Network Security, Network Security Protocols, Types of Network Security Solutions, Network Security Best Practices for Business,), Network Application Domain, Network Application Domain:
Network Attacks, Metasploit Framework, Metasploit Architecture, Exploitation using Metasploit, Computer Networks - Architecture, Layered architecture, Open Systems Interconnect (OSI) Model, Deep Packet Inspection (Intrusion detection system and Intrusion Prevention, System), IP Security, ICMP attacks, TCP and UDP Security. Attacking Availability: Denial-of-Service, attacks, Distributed DOS attacks, SSL/TLS
Access control, Security Vulnerability Management and Vulnerability Assessment, Remediation Planning, Encryption, Types of Encryptions, Encryption Algorithms and Protocols -
Data leakage
Data leakage and its types, NPI, Intellectual Property, Data Leak Vector, IM, Webmail, Data Classification, Content awareness, Content analysis techniques , DLP and its limitation,
-
Information Security Policies, Procedures, Standards and Guidelines
Information Security Policies, Top Information Security Threats (Unsecure or Poorly Secured Systems, Social Media Attacks, Social Engineering, Malware on Endpoints, Security Misconfiguration, Active and Passive Attack, Cyber Security Regulations, Roles of International Law, the INDIAN Cyberspace, National Cyber Security Policy 2013, Elements of an information security policy, Security standard and guideline , Cyber security Policy Management and Ecosystem, Cyber Security Frame Works, ISMS Environment
-
Information Security Management – Roles and Responsibilities & performance matrices
Elements, hierarchy and importance of Information security element of information security, Security Metrics, Types of Security Metrics, Mean-Time-to-Detect and Mean-Time-to-Respond
-
Risk Assessment
Introduction, Identification, role and need of to Risk Assessment,
-
Configuration Review
Configuration Management, Server Hardening, SecCM planning, CM tools (Solar Wind), Benefits of Configuration Management,
-
Device Log Correlation
Event correlation, use cases and techniques, benefits of event correlation, Key concept of log management, log management process and challenges,
-
Data Backup
Data backup and its types and Importance, RPO, RTO, Storage types, Backup Procedures,


