POPULAR
immersive learning
350 Hours
NASSCOM CYBER SECURITY PROGRAM
In an increasingly digital world, cyber security is crucial for protecting sensitive information and maintaining the integrity of computer systems and networks. It prevents unauthorized access to personal data, financial records, and intellectual property, ensuring that critical information remains secure. Effective cyber security measures also ensure business continuity by minimizing disruptions and financial losses caused by cyber attacks. Additionally, it helps maintain trust and reputation with customers and stakeholders, who expect their data to be handled securely. Compliance with regulatory requirements is another key reason why cyber security is essential, as it helps organizations avoid legal penalties and adhere to industry standards. Ultimately, robust cyber security is vital for safeguarding digital assets, supporting operational resilience, and upholding trust in the digital age.
OUR KNOWLEDGE PARTNERS








350 HOURS NASSCOM CYBER SECURITY PROGRAM
Cyber security is the practice of protecting systems, networks, and programs from digital attacks. In today’s digital landscape, with the increasing frequency and sophistication of cyber threats, mastering cyber security is more critical than ever. The NASSCOM Cyber Security Program is essential in equipping individuals with the knowledge and skills to combat these threats.
This official NASSCOM-CERTIFIED Cyber Security Program covers all the demanded tools of Cyber Security which includes Python, Java, AWS, OWASP, Burp Suite, Snort, Wireshark, Metasploit, and many more.
Tools
Program Structure
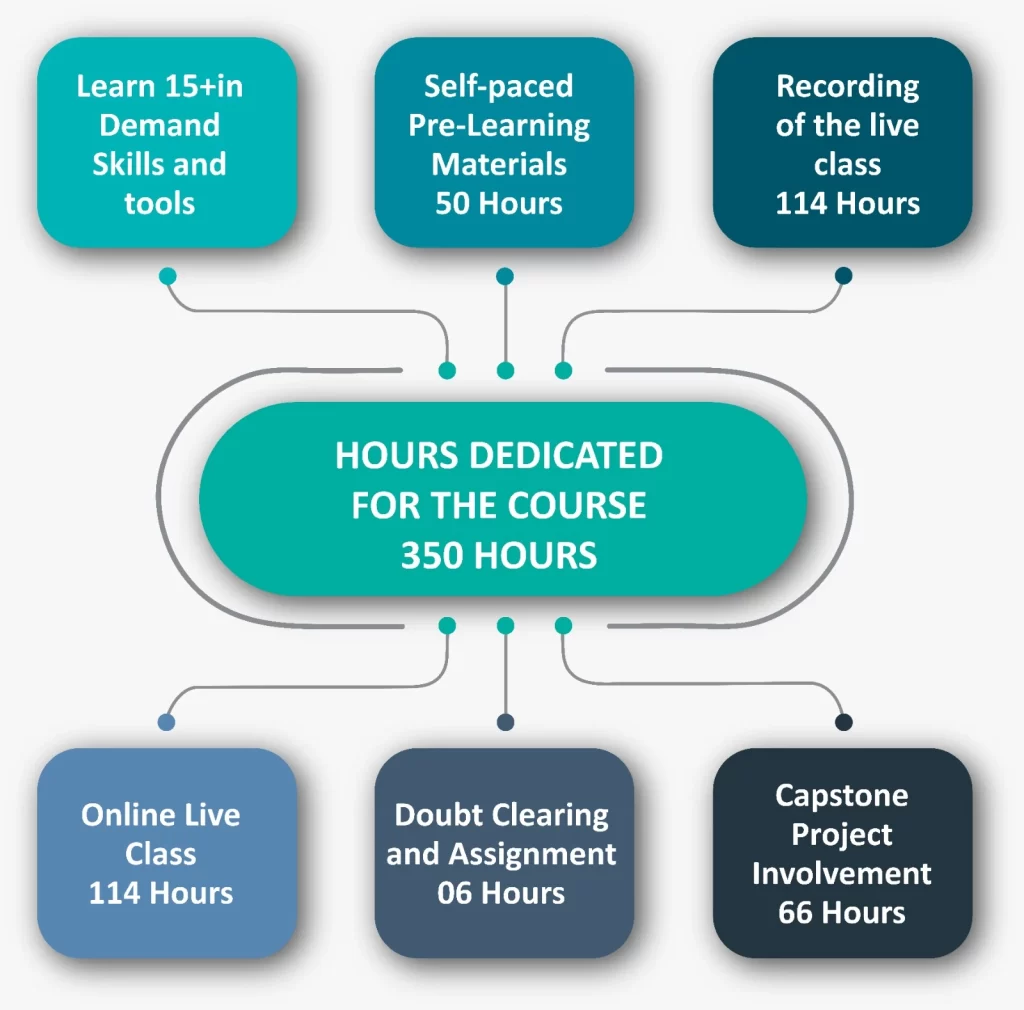
- 50 hour Pre-Learning: Before you embark on the live academic session, get ready for the Program. You will get a series of online recorded tutorials to understand the structure of Cyber security to know about the fundamentals which would enrich your future learning experience.
- 114 hours Program: Here, you will get execution-based learning experience on Python , Linux, information security, attack methodologies, web technologies, cryptography, network concepts, and incident handling.
- 6 hours Post Program:Learning does not stop here. After completing the modular training, you will work on Domain-specific Project , Assignments. Doubt clearing is also provided. You will be working on different capstone projects from a huge repository of data sets.
- 66-hours Capstone Project: After completing the main program, you will dedicate 66 hours to designing and developing your capstone project. This will allow you to apply all the skills and knowledge acquired throughout the course in a comprehensive, practical project.
lEARN WITH A WORLD CLASS CURRICULUM
Module 1. Information Security and Attack
- Day 1: What is Hacking ? , Computer Security Threats, Goals of Ethical Hacking, Skills and Tools required for Ethical Hackers,
Process of Ethical Hacking, Process of Ethical Hacking – Demonstration Part 1,Process of Ethical Hacking
– Demonstration Part 2. - Day 2: Information Gathering Concepts, Foot printing, Reconnaissance, Active Passive Scanning
- Day 3: CIA (Confidentiality, Integrity & Availability) Threat, Vulnerabilities, Threat Actor, Risk etc definitions & concept.
Advanced Cyber Security – Threats and Governance, What are Threats?, Types of threats (spoofing, tampering, repudiation,
information breach, DOS, elevation of privilege),GitHub DDos Attack,. - Day 4: Types of attack(DOS, Phishing, Ransomware).
- Day 5: Introduction and importance to information security, elements of information security (purpose, audience and scope,
security objective-CIA, Authority and access control, data classification (level 1-5), support and operation, security
awareness, responsibilities rights and duty. Principle of Information security (Confidentiality, Integrity, Availability). - Day 6: Introduction to data security, types of data security (Encryption, Data Erasure, Data Masking, Data Resiliency),
data security strategy (Physical security of servers and user devices, Access management and controls, Backups).
- 📚No. of Lectures: 6
- ⏳Duration of Lecture: 18 Hours
- 📝Assessment: 2
- 🌟Assignment: 1
- Day 7: Practical on Metasploit and bwap..
- Day 8: bWAPP Features, Why should you learn bWAPP?, bwapp prct.
- Day 9: Dvwa feature and use.
- Day 10: Kali Linux (tool) Demonstration – Web Application attack: Broken Authentication,
Demonstration – Web Application attack: Blind SQL Injections, Demonstration – Web Application attack: Cross site scripting. - Day 11: Web Application Domain, Web Application Domain: Common Attacks, Hacking Methodology,.
- Day 12: Mobile Application Domain, Mobile Application Domain: Types of Android Attacks, steps of Incident preventation, network
reconnaissance incidents (host detection, port enumeration, vulnerability assessment), DoS, Malicious Code,. - Day 13: Information gathering (Spiders, Robots and Crawlers/Search Engine Discovery/Reconnaissance/Testing Web Application
Fingerprint/. Analysis of Error Codes:) .
- 📚No. of Lectures: 7
- ⏳Duration of Lecture: 21 Hours
- 📝Assessment: 2
- 🌟Assignment: 1
- Day 14: “Remediation Planning, Encryption, What is Encryption?, Prerequisites for Encryption, How does Encryption work?,
Vulnerability Assessment”. - Day 15:“What is Decryption? , Encryption Vs Decryption, Types of Encryption, Encryption Algorithms and Protocols,
Web application architecture, Web application attacks, Web server architecture, Web server attacks”.
- 📚No. of Lectures: 2
- ⏳Duration of Lecture: 6 Hours
- 📝Assessment: 1
- 🌟Assignment: 1
- Day 16: “Introduction to information security controls, types of controls (organizational control, people control, physical control,
technological control), preventive, corrective and digestive control,”. - Day 17: OSI concept, Protocols, ARP, SMTP, ICMP, TCP, 3 way Handshaking.
- Day 18: “Security Market Outlook, Computer Networks – Architecture, Layered architecture, Open Systems Interconnect (OSI) Model,
Transmission Control Protocol/Internet Protocol (TCP/IP), Network Scanning, Enumeration, Common Network
Threats/Attacks, Packet Inspection,”. - Day 19: Deep Packet Inspection(Intrusions detection system and Intrusion Prevention, System), IP Security, ICMP attacks.
- Day 20: “TCP and UDP Security. Attacking Availability: Denial-of-Service, attacks, Distributed DOS attacks, SSL/TLS Data/Application
Security: confidentiality, Integrity, availability, authorization, authentication, identification, non-repudiation, types of control
(preventive, detective, corrective, deterrent, recovery, compensating), access control, Security Vulnerability Management”. - Day 21: “Network devices (Hub, Switch, Router, Bridge, Gateway, Modem, Repeater, Access Point), Configuration of network devices,
Network configuration tool, Firewall, Firewall configuration,”.
- 📚No. of Lectures: 6
- ⏳Duration of Lecture: 18 Hours
- 📝Assessment: 2
- 🌟Assignment: 2
- Day 22: “Introduction to data leakage (direct losses and indirect losses.), Types of Data Leakage, NPI
(e.g. Customer Data), Confidentiality Info, PHI (e.g. Patient’s Records),Intellectual Property, Data
Leak Vector :- HTTP, Email, Networked Printer, End Point, Internal Mail,”. - Day 23: IM, Webmail, Data Classification, types of data classification, steps and process of data classification,.
- Day 24: “Content awareness, Content analysis techniques (rule based, data based finger printing, partial document
matching, lexicon), DLP (data in motion, data in rest, data in use), DLP limitation, DLP using DRM,”. - Day 25: “DEFINITION OF EVENT CORRELATION, EVENT CORRELATION USE CASES AND TECHNIQUES,
BENEFITS OF EVENT CORRELATION, Event log,”. - Day 26: “Key concept of log management (log, event, incidents), log management process and challenges,
configuration of windows event log, SIEM, Remote Software Access, Web Proxies, Firewall, Routers.”. - Day 27: “What is Data backup, Importance of data backup, why to backup, RPO, RTO, Types (Mirror, Full,
Differential, incremental backup, Cloud Backup, FTP backup,),”. - Day 28: “Storage types (local or USB Disks, Network Shares and NAS, Data Backup to Tapes, Cloud Storage, ),
Backup Procedures,”.
- 📚No. of Lectures: 7
- ⏳Duration of Lecture: 21 Hours
- 📝Assesment: 2
- 🌟Assignment: 2
- Day 29: Information Security Policy, Top Information Security Threats (Unsecure or Poorly Secured Systems,
Social Media Attacks, Social Engineering, Malware on Endpoints, Lack of Encryption,. - Day 30: Security Misconfiguration, Active and Passive Attack, Cyber Security Regulations, Roles of International Law, the state and Private Sector in Cyberspace, Cyber Security Standards. The INDIAN Cyberspace, National Cyber Security Policy 2013. Elements of an information security policy (Purpose, scope, Objective, authorization and access control, classification, data support operation, Security standard and guideline(COSO, COBIT,ITIL, NIST, NSA, ISO, IT act, Copyright, Patent law, IPR), Laws of Indian Govt.,.
- Day 31: Cyber Security Landscape Cyber security Policy Management , Cyber Security Policy Ecosystem, Cyber Security Policy ,Management Design, Cyber Security FrameWorks, ISMS Environment, Frameworks, ISO27001 Standard.
- Day 32: Security Metrics, Types of Security Metrics (Strategic security metrics, Security management metrics,Operational security
metrics), Mean-Time-to-Detect and Mean-Time-to-Respond, Number of systems with known vulnerabilities, Number of
SSL certificates configured incorrectly,Volume of data transferred using the corporate network,. - Day 33: Number of communication ports open during a period of time, Frequency of review of third-party accesses, frequency of
access to critical enterprise systems by third parties, Percentage of business partners with effective cybersecurity policies. - Day 34: Introduction to Risk Assessment, Identification of Risk assessment, Risk assessment model (Identification, Assessment,
Mitigation, Preventation), role and need of risk assessment”.
- 📚No. of Lectures: 6
- ⏳Duration of Lecture: 21 Hours
- 📝Assesment: 1
- 🌟Assignment: 1
- Day 35: Hierarchy of Information security (Board of Director, CIO, CISO, CEO, System Architect, System Engineer, Security
Director, System Admin, Security Analyst, IS Auditor, DB Admin), Importance of information security policy, element
of information security (purpose, audience, CIA, encryption policy, data backup policy,.
- 📚No. of Lectures: 1
- ⏳Duration of Lecture: 3 Hours
- 📝Assesment: 0
- 🌟Assignment: 0
Module 2. CAPSTONE PROJECT
- Keylogger Software
- Network Traffic Analyser
- Password Analyser and many more
SKILLS YOU WILL POSSESS
✔️ Python and Linux
✔️ Data Analysis
✔️ Web Scraping and Automation
✔️ Information Security and Ethical Hacking
✔️ Web Technologies and OWASP
✔️ CryptographyNetwork Security
✔️ Data Management and DLP
✔️ Compliance and Risk Management
✔️ Incident Handling and Security Operations
✔️ Information Security Audit
PROGRAM BENEFITS
✔️ Cutting Edge Curriculum: Hand crafted Course content made by Experts from various Industries. Learn through Practical case studies and multiple projects.
✔️ On the Go Learning: Online accessible E-learning Material, recorded lectures, case studies and Research Paper through our system.
✔️ Build Solid Foundation: 195 hours focused course on CYBER SECURITY.
✔️ Industry Mentorship: Get 1 to 1 guidance from Industry experts and start your career in Cyber Security.
✔️ Earn a Government of India approved & globally recognized certificate by NASSCOM IT- ITes SSC by clearing NASSCOM assessment examination.
Course Certificates
Career Services By emergingindiagroup

Placement Assistance
Exclusive access
Mock Interview Preparation
1 on 1 Career Mentoring Sessions
Career Oriented Sessions
Resume & LinkedIn Profile Building
Real World Projects
Projects will be a part of Our 600 Hours Nasscom Certified Full Stack Cyber Security Program to solidify your learning. They ensure you have real-world experience in Development and Operations.
- Practice 25+ Essential Tools
- Designed by Industry Experts
- Get Real-world Experience
Our Alumni Works At














Learners thought about us




Admission Details

Submit Application
Tell us a bit about yourself and why you want to join this program

Application Review
An admission panel will shortlist candidates based on their application

Admission
Selected candidates will be notified within 1week.
Program Fees
Our Loan Partners






Zero Cost EMI options Available
from RBI Approved NBFCs
Starting from ₹2,999*
Others Payment Options
Internet Banking
Credit / Debit Card
Total Admission Fees
₹58,999*(Including GST)
USD $899
faQS
The duration of the NASSCOM Cyber Security Program is 350 hours, covering a comprehensive curriculum ranging from foundational topics in Python and Linux to advanced concepts in cryptography, network security, incident handling, and practical applications in cybersecurity tools and techniques.




